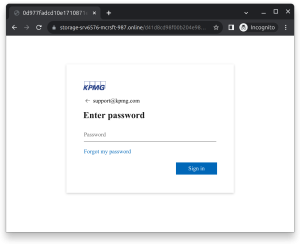
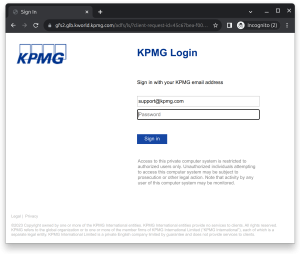
Sophisticated Phishing
Observations
WARNING: Do not put credentials into this URL. We extracted the following URL from a Docusign phishing email QR code. The URL links to an embedded cloudflare tenant, with a domain registered in India, and appears to be doing a MITM (Man-In-The-Middle) on Microsoft IDPs (Identity Providers). The URL https://storage-srv6576-mcrsft-987.online/ appears to pull and/or proxy the legitimate content resources from customized Office 365 IDPs to make the presented login page appear like a legitimate microsoft site. Some screen captures of this are shown below.
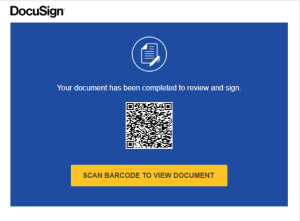
This first image is part of the original email content, which was made to look like a legitimate Docusign email with an embedded QR code that we extracted out of curiousity. To our surprise, it looks like it might be a sophisticated credential grabber, but we have not explored or tested it beyond capturing the observations in this post to be used as an educational tool for some of our clients.
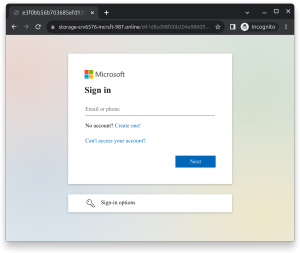
This second image below shows the Cloudflare tenant website https://storage-srv6576-mcrsft-987.online/ that the QR code takes the user to. Most unsuspecting users would believe it to be a standard microsoft Identity Provider prompt and enter their username to proceed with authentication. Even the clever wording of the .online URL may seem unsuspecting to some users.
In the image below, we used a known Microsoft 365 customer ING, to show what happens next if you enter an email from a domain using M365 authentication. What happens is that this Cloudflare tenant finds the real Identity Provider landing page and builds a legitimate (but fake) page using resources from the customized Microsoft Identity Provider site. On this fake page, none of the links work, which is another clue that it is not legitimate. It does use of the same background images and logo from the original Mircosoft site. This is the worrisome part, as you can see that it appears very similar to the actual ING login site shown in the next screenshot.
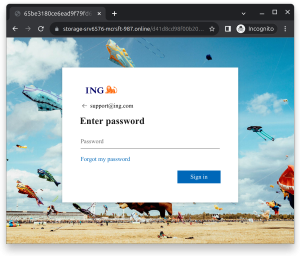
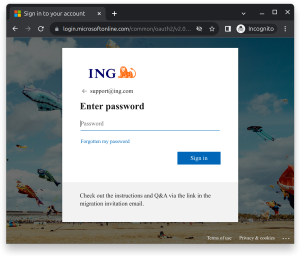
In the image below, this is what the actual ING Office 365 login site looks like when the user “support@ing.com” is entered into the actual Mircosoft Office 365 sign-in page. Notice how similar the illegitimate and legitimate sites appear. Only the URL and functional links to the forgotten password page differentiate this to the average user.
We tested another well know brand and Office 365 user KPMG. In this case, their simple, but more customized, IDP landing page yeilded a much larger difference between the the forged clone (immediately below) and the legitimate site (shown at the bottom). Changing the layout of the login page is a strategy that may help users identify the difference between real Microsoft login pages and clever clones made to look like the uncustomized default.